
New security vulnerabilities threaten Apple chips: what you need to know
Technical universities from the USA and Germany discover "SLAP" and "FLOP". These two security vulnerabilities threaten all Apple chips from M2 onwards as well as some A processors. Apple reacts hesitantly.
"SLAP" and "FLOP" are the names of the two security vulnerabilities that are currently threatening the security of various Apple devices. This was announced at the beginning of the week. All devices equipped with an M2 chip or newer could potentially be affected. However, these two vulnerabilities could also be exploited in mobile processors A15 and newer.
What exactly do "SLAP" and "FLOP" do?
"SLAP" stands for "Speculation Attacks via Load Address Prediction" and concerns the so-called "Load Address Predictor".
This "Load Address Predictor" is responsible for predicting which memory address the processor will need next. The "SLAP" vulnerability causes it to make false predictions. This means that malicious code introduced via "SLAP" can access memory areas where it has no business being. This could theoretically allow attackers to access data on your devices.
The "FLOP" stands for "False Load Output Predictions" and relates to the "Load Value Predictor". This tries to predict which values will be returned from the memory in which the processor has stored data. Modern chips do this so that operations are carried out faster and more efficiently. However, if the "FLOP" comes into play, it could deliver incorrect values to the "Load Value Predictor" and thus circumvent security mechanisms.
Theoretically, an end-to-end attack on Safari is therefore possible. Or, for example, via email content that is loaded from external servers via HTTP.
If you are interested in the technical details - such as where access can take place - you can find them in the discoverers' report here.
Apple seems relaxed
Apple categorises the two vulnerabilities as "no immediate risk to users". Although the company was made aware of the problems by Ruhr University Bochum and a university in the US state of Georgia in September 2024, they have not yet patched the vulnerabilities. At present, this has apparently not yet been actively exploited - but this could theoretically happen at any time.
Source: Florian Bodoky
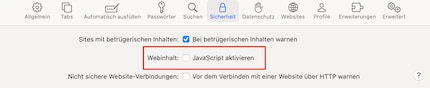
Until the patch arrives, you could, for example, disable the JavaScript function in Safari (Safari>Preferences>Security>Uncheck JavaScript). However, this is only worthwhile for experienced users, because: It helps against the attacks, but will sometimes cause problems with many websites. It is therefore worth checking regularly whether Apple has updates available.
I've been tinkering with digital networks ever since I found out how to activate both telephone channels on the ISDN card for greater bandwidth. As for the analogue variety, I've been doing that since I learned to talk. Though Winterthur is my adoptive home city, my heart still bleeds red and blue.
From the latest iPhone to the return of 80s fashion. The editorial team will help you make sense of it all.
Show all